Difference between revisions of "Active Directory - Set up Role Mappings"
(→Role Mapping) |
|||
| Line 1: | Line 1: | ||
[[Category:How_To]] | [[Category:How_To]] | ||
=Overview= | =Overview= | ||
| − | If you are using Active Directory as the Authentication Service you will need to access the Role Mapping option from the Server Security Menu which is available to logged-in users. This page maps the Organisations you have set up in the Registry to the Groups and users that you have created in Active Directory. | + | If you are using Active Directory as the Authentication Service, you will need to access the Role Mapping option from the Server Security Menu which is available to logged-in users. This page maps the Organisations you have set up in the Registry to the Groups and users that you have created in Active Directory. |
=Example Use Case= | =Example Use Case= | ||
| − | In this very simple example the following has taken place... | + | In this very simple example, the following has taken place... |
==Server Security - General == | ==Server Security - General == | ||
| Line 71: | Line 71: | ||
===Results=== | ===Results=== | ||
| − | Having created the 3 mappings the Role Mappings | + | Having created the 3 mappings, the Role Mappings page will display a line for each Organisation (this is the counter intuitive aspect referred to as above). If you click on any of the Data Consumer records or any of the Data Provider records you will see that they are all the same insofar as all 3 are shown. |
Revision as of 04:30, 8 March 2021
Contents
Overview
If you are using Active Directory as the Authentication Service, you will need to access the Role Mapping option from the Server Security Menu which is available to logged-in users. This page maps the Organisations you have set up in the Registry to the Groups and users that you have created in Active Directory.
Example Use Case
In this very simple example, the following has taken place...
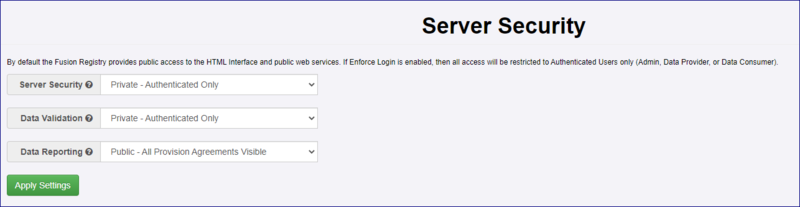
Server Security - General
The Registry has been fully locked-down so only authorised users are able to login. You can read more about the general concepts of Security in Fusion Registry in this article.
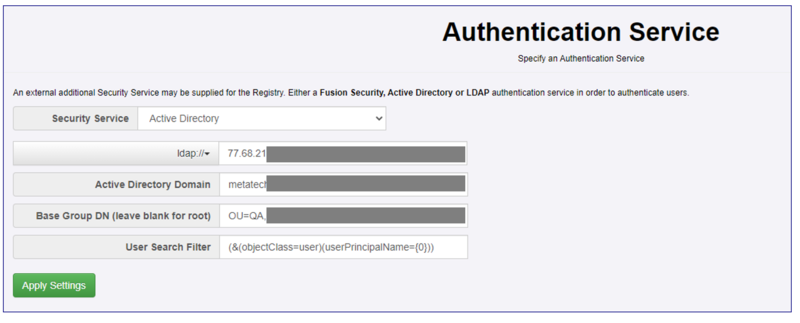
Server Security - Authentication Service
The relevant settings for active Directory (in this instance idap is used rather than idaps) have been applied.
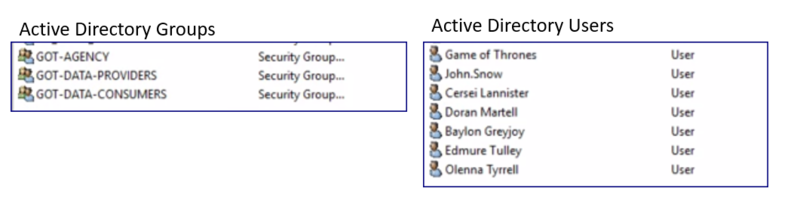
Active Directory
3 Groups have been created, one for each type of user:
- Agency
- Data Provider
- Data Consumer
7 Users have been created. Game of Thrones is the Agency, John, Cersei and Doran are Data Providers and Baylon, Edmure and Olenna are Data Consumers. Each of the users is a member of the appropriate group.
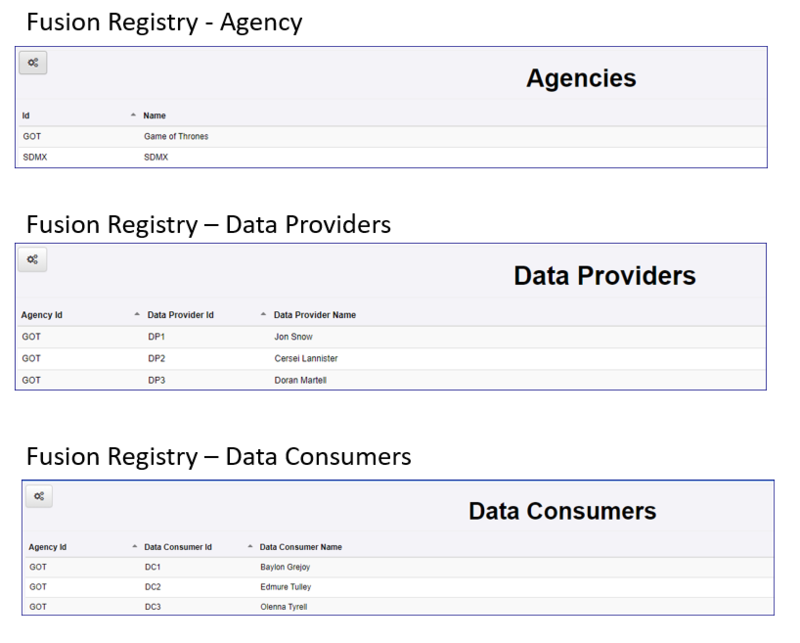
Fusion Registry
In the Organisations area of Fusion Registry, again 7 records exist, the Agency, the 3 Data Providers and the 3 Data Consumers.
Role Mapping
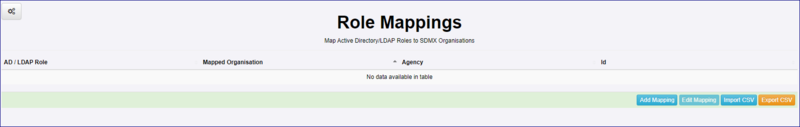
The Role Mapping page is where you specify which Groups in AD map to which Organisations in Fusion Registry. At the moment this page is somewhat counter-intuitive (which we plan to address in a future release), but if you follow the steps below, your mapping will succeed.
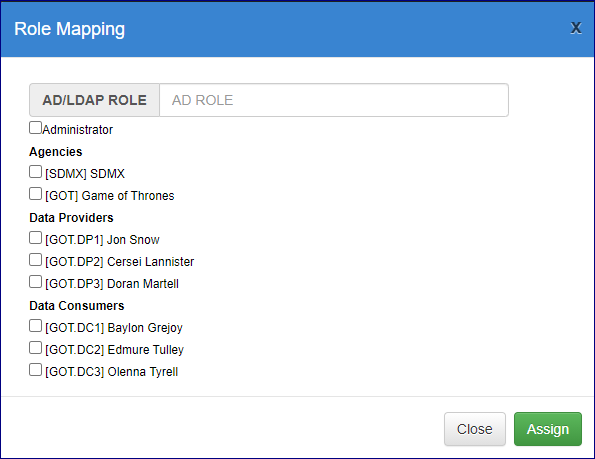
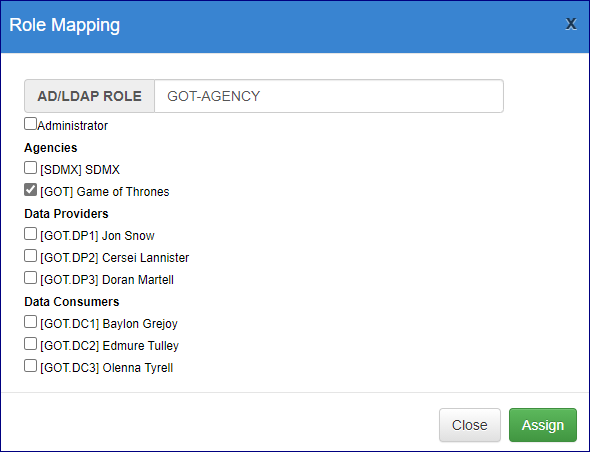
Map the Agency
In the Role Mappings page, click the Add Mapping button. The Role Mapping modal will appear and display all the Organisations in the Registry.
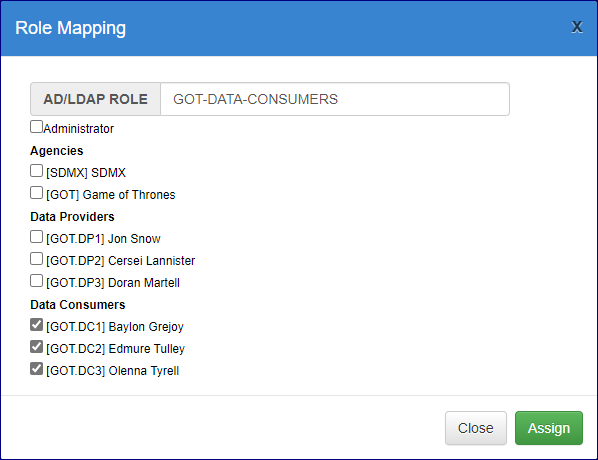
In the field AD Role, enter the Group name exactly as it appear in AD and then select the Agency as shown in the image below.
Click Assign to return to the Role Mapping page.
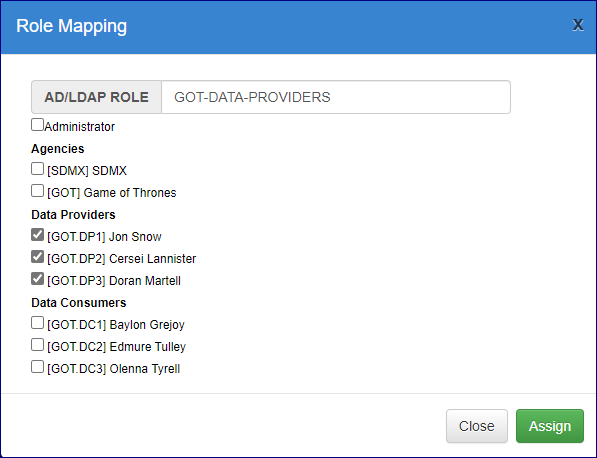
Map the Data Providers
Again, click the Add Mapping button and enter the AD Group name but this time you can click all three Data Providers as shown on the example below.
Map the Data Consumers
Click all the Data Consumers and then click Assign.
Results
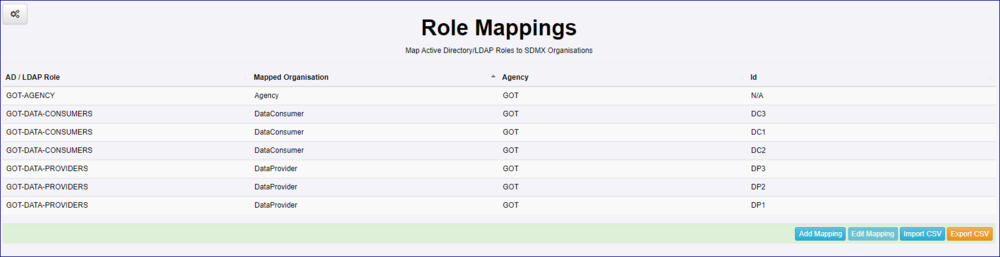
Having created the 3 mappings, the Role Mappings page will display a line for each Organisation (this is the counter intuitive aspect referred to as above). If you click on any of the Data Consumer records or any of the Data Provider records you will see that they are all the same insofar as all 3 are shown.
However, the mapping has been successful and all 7 AD users will be able to login to the Registry and will have the correct privilege's as discussed in this article.
Click here to learn about other functions available in the Role Mapping page.