Difference between revisions of "How Registry Interfaces With Active Directory"
(→Unsuccesfull Access) |
|||
| (24 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | Active Directory can be used as the security manager for Fusion Metadata Registry. | + | [[Category:Installation_and_Configuration]] |
| + | [[Category:RegistrySecurity]] | ||
| + | [[Category:FMR_Configuration_Reference]] | ||
| + | [[Category:How_To]] | ||
| + | Active Directory can be used as the security manager for Fusion Metadata Registry which is defined [[Security_Configuration|here]]. Once Active Directory has been set as the security manager, the role mappings which associate Active Directory groups to roles in the Registry needs to be defined and this is explained [[Active_Directory_-_Set_up_Role_Mappings|here]]. | ||
| + | For a Fusion Metadata Registry which has an Active Directory successfully configured, this page explains how the two systems communicate. | ||
=Invalid Credentials= | =Invalid Credentials= | ||
| − | + | If the user provides incorrect credentials to the Fusion Registry, the following communication takes place: | |
[[File:AD-Unsuccessful.png]] | [[File:AD-Unsuccessful.png]] | ||
| − | |||
| − | |||
1) The Registry receives an HTTP (or HTTPS) Servlet Request from the browser. This request carries the username and password as supplied from the login page of the Registry.<br> | 1) The Registry receives an HTTP (or HTTPS) Servlet Request from the browser. This request carries the username and password as supplied from the login page of the Registry.<br> | ||
2) From this request object, an Authentication token is created within the Registry and sent as an LDAP (or LDAPS) connection to the Active Directory server. This token only contains the userid and password as supplied in the previous stage. | 2) From this request object, an Authentication token is created within the Registry and sent as an LDAP (or LDAPS) connection to the Active Directory server. This token only contains the userid and password as supplied in the previous stage. | ||
| − | The Naming Manager | + | The Naming Manager aspect of Active Directory attempts to resolve the supplied credentials. |
<br> | <br> | ||
| − | 3) Since the credentials were not authorised by the Naming Manager, Active Directory responds with an LDAP (or LDAPS) response | + | 3) Since the credentials were not authorised by the Naming Manager, Active Directory responds with an LDAP (or LDAPS) response informing of the incorrect credentials <br> |
| − | 4) Fusion Registry responds to the browser with an HTTP Servlet Response containing the information that the authentication request was | + | 4) Fusion Registry responds to the browser with an HTTP Servlet Response containing the information that the authentication request was unsuccessful, along with a status code for the reason.<br> |
| − | = | + | =Successful Access= |
| − | + | If the user provides the correct credentials to the Fusion Registry and a valid mapping has been defined to map the user's Active Directory groups to that of Fusion Registry, the following communication takes place: | |
| − | |||
| − | |||
| − | |||
| + | [[File:AD-Successful.png]] | ||
| + | 1) The Registry receives an HTTP (or HTTPS) Servlet Request from the browser. This request carries the username and password as supplied from the login page of the Registry.<br> | ||
| + | 2) From this request object, an Authentication token is created within the Registry and sent as an LDAP (or LDAPS) connection to the Active Directory server. This token only contains the userid and password as supplied in the previous stage. | ||
| + | The Naming Manager aspect of Active Directory attempts to resolve the supplied credentials. | ||
| + | <br> | ||
| + | 3) The credentials are authorised within Active Directory and it responds with an LDAP (or LDAPS) response stating the credentials are correct.<br> | ||
| + | 4) The Fusion Registry issues another request to Active Directory, specifying the search and filter criteria (along with the authenticated Principal).<br> | ||
| + | 5) Active Directory uses the search information, which was supplied when the Active Directory connection was definied in the Fusion Registry, to obtain information regarding the user. This is essentially which groups the user is a member of.<br> | ||
| + | 6) Fusion Registry constructs a UsernamePasswordAuthenticationToken which defines what organisations the user can access, and responds to the browser with an HTTP Servlet Response containing the information that the authentication request was successful.<br> | ||
| − | + | =User has no Permissions within the Registry= | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | This | + | In the scenario where a user provides valid Active Directory credentials but the user, as defined within Active Directory, has no permissions in the Registry then the flow of communication follows the same sequence of events as successful access up to stage 5. This is because the user has provided credentials that Active Directory has validated as correct. The groups for this user are supplied back to Fusion Registry and are checked within the "Fusion Granted Authority" of the Registry. Since there are no roles for this user to perform, a "NoRolesException" is thrown and a response is sent from the Fusion Registry to the web browser that this user has no permissions within Fusion Registry. The user is therefore not granted access to Fusion Metadata Registry. |
| − | |||
Latest revision as of 03:33, 30 March 2024
Active Directory can be used as the security manager for Fusion Metadata Registry which is defined here. Once Active Directory has been set as the security manager, the role mappings which associate Active Directory groups to roles in the Registry needs to be defined and this is explained here.
For a Fusion Metadata Registry which has an Active Directory successfully configured, this page explains how the two systems communicate.
Invalid Credentials
If the user provides incorrect credentials to the Fusion Registry, the following communication takes place:
1) The Registry receives an HTTP (or HTTPS) Servlet Request from the browser. This request carries the username and password as supplied from the login page of the Registry.
2) From this request object, an Authentication token is created within the Registry and sent as an LDAP (or LDAPS) connection to the Active Directory server. This token only contains the userid and password as supplied in the previous stage.
The Naming Manager aspect of Active Directory attempts to resolve the supplied credentials.
3) Since the credentials were not authorised by the Naming Manager, Active Directory responds with an LDAP (or LDAPS) response informing of the incorrect credentials
4) Fusion Registry responds to the browser with an HTTP Servlet Response containing the information that the authentication request was unsuccessful, along with a status code for the reason.
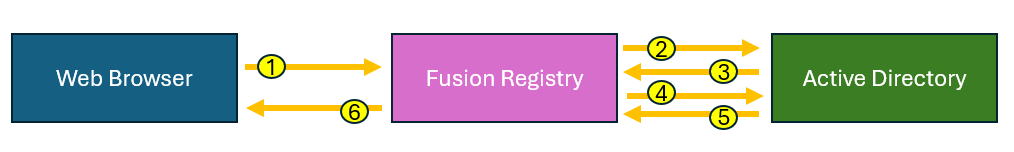
Successful Access
If the user provides the correct credentials to the Fusion Registry and a valid mapping has been defined to map the user's Active Directory groups to that of Fusion Registry, the following communication takes place:
1) The Registry receives an HTTP (or HTTPS) Servlet Request from the browser. This request carries the username and password as supplied from the login page of the Registry.
2) From this request object, an Authentication token is created within the Registry and sent as an LDAP (or LDAPS) connection to the Active Directory server. This token only contains the userid and password as supplied in the previous stage.
The Naming Manager aspect of Active Directory attempts to resolve the supplied credentials.
3) The credentials are authorised within Active Directory and it responds with an LDAP (or LDAPS) response stating the credentials are correct.
4) The Fusion Registry issues another request to Active Directory, specifying the search and filter criteria (along with the authenticated Principal).
5) Active Directory uses the search information, which was supplied when the Active Directory connection was definied in the Fusion Registry, to obtain information regarding the user. This is essentially which groups the user is a member of.
6) Fusion Registry constructs a UsernamePasswordAuthenticationToken which defines what organisations the user can access, and responds to the browser with an HTTP Servlet Response containing the information that the authentication request was successful.
User has no Permissions within the Registry
In the scenario where a user provides valid Active Directory credentials but the user, as defined within Active Directory, has no permissions in the Registry then the flow of communication follows the same sequence of events as successful access up to stage 5. This is because the user has provided credentials that Active Directory has validated as correct. The groups for this user are supplied back to Fusion Registry and are checked within the "Fusion Granted Authority" of the Registry. Since there are no roles for this user to perform, a "NoRolesException" is thrown and a response is sent from the Fusion Registry to the web browser that this user has no permissions within Fusion Registry. The user is therefore not granted access to Fusion Metadata Registry.