Difference between revisions of "Authentication Service"
(Created page with "==Overview== The administration page to set the Authentication Service of FMR has controls for the different security services. Use the drop-down at the top of the page to sel...") |
(→Testing the Active Directory Settings) |
||
| (45 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| + | [[Category:RegistrySecurity]] | ||
| + | [[Category:How_To_V11]] | ||
==Overview== | ==Overview== | ||
The administration page to set the Authentication Service of FMR has controls for the different security services. Use the drop-down at the top of the page to select the service you require. The current options are: | The administration page to set the Authentication Service of FMR has controls for the different security services. Use the drop-down at the top of the page to select the service you require. The current options are: | ||
| Line 7: | Line 9: | ||
===Configuring Active Directory=== | ===Configuring Active Directory=== | ||
| + | |||
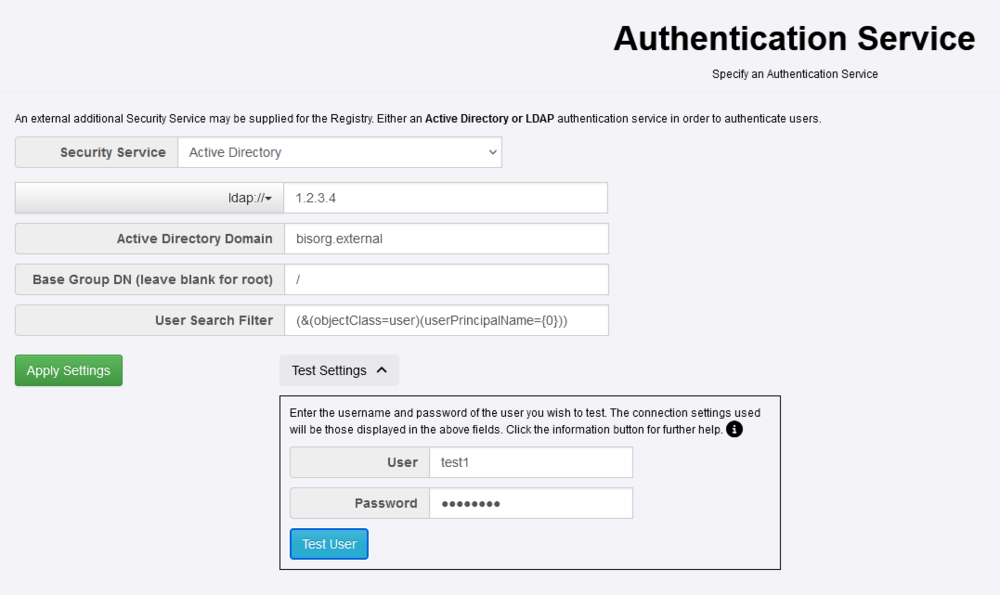
| + | When Active Directory has been chosen as the Authentication Mechanism, the following information needs to be provided | ||
| + | |||
| + | [[File:AuthenticationService-ShowingActiveDirectory.png|Authentication Set-up|1000px]] | ||
| + | |||
| + | * The protocol type: either ldap or ldaps | ||
| + | * The IP address or name of the server hosting the Active Directory instance | ||
| + | * The Active Directory Domain Name - this can be obtained from the Active Directory administration tool | ||
| + | * The Base Group Domain Name (optional) | ||
| + | * The User Search Filter (optional) | ||
| + | |||
| + | The 2 values which are sometimes the most difficult to define are the Base Group Domain Name and the User Search Filter. If these are specified incorrectly, then even though FMR is communicating with your Active Directory instance correctly, then you may find users are unable to login. | ||
| + | |||
| + | ====Base Group Domain Name==== | ||
| + | The value here can be left blank, in which case the root of the Active Directory tree will be used as the root of searching for users. However to be more specific you can specify the Organizational Units (OU) and Domain Components (DC) to search within. It is likely you will need to specify the Domain Components. Please note that the order of the components is very important here. | ||
| + | |||
| + | When specifying OUs they are typically listed in reverse order, with the lowest-level OU specified first which aligns with the hierarchical nature of how these units are defined within AD. The DC elements are listed in a more natural left-to-right order. | ||
| + | |||
| + | By way of example, if you wished to search in the Domain Component "bisorg.external" and under that domain, there was the hierarchy of the Organizational Unit "fusion" with the Organizational Unit "Registry" within that, then the following string, with its elements in the following order, would be used: | ||
| + | <pre> | ||
| + | OU=Registry,OU=fusion,DC=bisorg,DC=external | ||
| + | </pre> | ||
| + | |||
| + | ====User Search Filter==== | ||
| + | This field determines how the FMR will locate users within the AD tree. The syntax of valid values can be located on the Microsoft support site. FMR will not validate the contents of this field for syntactical correctness and will simply use what is entered. | ||
| + | |||
| + | If this field is left blank, the following value will be used: | ||
| + | |||
| + | <code> | ||
| + | (&(objectClass=user)(userPrincipalName={0})) | ||
| + | </code> | ||
| + | |||
| + | This states that the search filter is looking for objects in Active Directory of class "user" and where the User Principal Name of those objects is the value as specified by {0}. {0} is a placeholder for the value the user types in to FMR in order to become authenticated, however there are some subtleties. In the User Search field there are two placeholder values: | ||
| + | * {0} - is the "bind principal". This is the username that the user types into the login dialog (when attempting to login). However if this value does NOT contain an "@", then the domain name is appended to it. For example, if the user attempts to log in as "Alice", on the domain "bisorg.external", then the value that replaces {0} will be Alice@bisorg.external | ||
| + | * {1} - is the "username" only. This corresponds exactly to the username. If the user attempts to log in as "Alice", then the value that replaces {1} will be simply "Alice". | ||
| + | |||
| + | By way of example, the following specifies a search for objects of class "user" where the User Principal Name in AD will be the "bind principal". If this is not resolved, then the sAMAccountName is checked against the username: | ||
| + | |||
| + | <code> | ||
| + | (&(objectClass=user)(|(userPrincipalName={0})(sAMAccountName={1}))) | ||
| + | </code> | ||
| + | |||
| + | ===Testing the Active Directory Settings=== | ||
| + | Since it can be difficult to set the Active Directory settings correctly, since version 11.17.0 of FMR, there is also the ability from this page for an Admin user of FMR to test how Active Directory would respond with an attempted log-on for a particular user. This feature allows for quicker investigation and resolution of the Active Directory settings that you will require for your environment. | ||
| + | |||
| + | Clicking the "Test Settings" control displays a section of the page allowing the systems admin to enter a userid and password. Note that the other AD settings can be modified during this time allowing for experimentation. | ||
| + | |||
| + | When the blue "Test User" button is clicked , the system attempts to authenticate the user specified in the lower section. Here are some sample responses: | ||
| + | |||
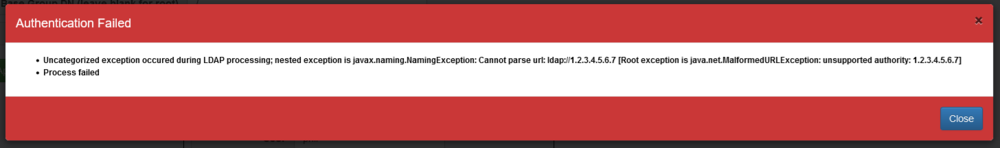
| + | '''Examples of unable to communicate with the AD system:''' | ||
| + | |||
| + | [[File:Test-ADUser-06-Fail.png|Authentication Set-up|1000px]] | ||
| + | <br> | ||
| + | <br> | ||
| + | [[File:Test-ADUser-07-Fail.png|Authentication Set-up|1000px]] | ||
| + | <br> | ||
| + | <br> | ||
| + | |||
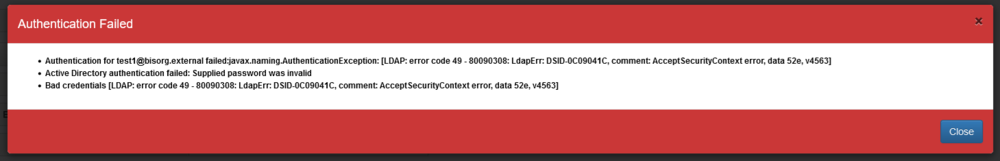
| + | '''Example of incorrect password for the user:''' | ||
| + | |||
| + | [[File:Test-ADUser-01.png|Authentication Set-up|1000px]] | ||
| + | <br> | ||
| + | <br> | ||
| + | '''Example of incorrect AD - the user couldn't be located since the Base Group DN was incorrect:''' | ||
| + | |||
| + | [[File:Test-ADUser-02.png|Authentication Set-up|1000px]] | ||
| + | <br> | ||
| + | <br> | ||
| + | '''Example of too many users being found. There must be a unique user for the specified userid''' | ||
| + | |||
| + | [[File:Test-ADUser-03.png|Authentication Set-up|1000px]] | ||
| + | <br> | ||
| + | <br> | ||
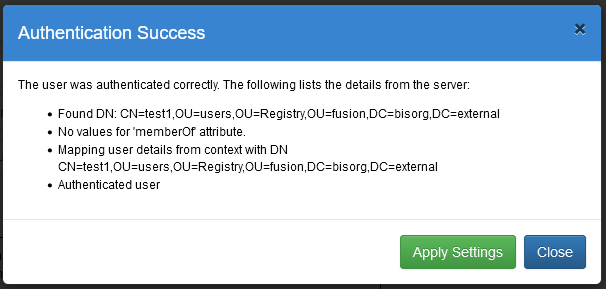
| + | '''Example of correct credentials:''' | ||
| + | |||
| + | [[File:Test-ADUser-04-Success.png|Authentication Set-up]] | ||
| + | <br> | ||
| + | <br> | ||
| + | |||
| + | ===Other Active Directory Tools=== | ||
| + | If you are still having issues determining what your settings should be for Active Directory, then the Windows Powershell commands "'''Get-ADUser'''" and "'''dsquery'''" may be useful to you. | ||
| + | |||
| + | '''dsquery''' is a command-line tool in Windows operating systems used to query the Active Directory directory service. Active Directory is a service developed by Microsoft that provides centralized authentication, authorization, and directory services for Windows-based networks. The dsquery command allows administrators to search and retrieve information from Active Directory. It can be used to find various objects such as users, groups, computers, and organizational units (OU). | ||
| + | |||
| + | If you wish to find a particular user, you can use the command: | ||
| + | |||
| + | <pre> | ||
| + | dsquery user -samid <username> | ||
| + | </pre> | ||
| + | |||
| + | It can also allow you to test your search filter, such as in the following manner, which obtains the Base Group DN for the user 'test1' | ||
| + | |||
| + | <pre> | ||
| + | dsquery * domainroot -filter "(&(objectClass=user)(userPrincipalName=test1*))" | ||
| + | |||
| + | "CN=test1,OU=users,OU=Registry,OU=fusion,DC=bisorg,DC=external" | ||
| + | </pre> | ||
| + | |||
| + | |||
| + | The Windows PowerShell command '''Get-ADUser''' allows the retrieval of a user's information. So to see what the sAMAccountName is for a particular user, you can use: | ||
| + | <pre> | ||
| + | Get-ADUser -Identity "username" | Select-Object SamAccountName | ||
| + | </pre> | ||
| + | |||
| + | ===Next Steps=== | ||
| + | It is likely that you will wish to create Role Mappings for your users. Please refer to [[Active_Directory_-_Set_up_Role_Mappings|the Role Mappings page]] for further information. | ||
Latest revision as of 08:22, 21 May 2024
Contents
Overview
The administration page to set the Authentication Service of FMR has controls for the different security services. Use the drop-down at the top of the page to select the service you require. The current options are:
- None
- Active Directory
- LDAP
- Fusion Security
Configuring Active Directory
When Active Directory has been chosen as the Authentication Mechanism, the following information needs to be provided
- The protocol type: either ldap or ldaps
- The IP address or name of the server hosting the Active Directory instance
- The Active Directory Domain Name - this can be obtained from the Active Directory administration tool
- The Base Group Domain Name (optional)
- The User Search Filter (optional)
The 2 values which are sometimes the most difficult to define are the Base Group Domain Name and the User Search Filter. If these are specified incorrectly, then even though FMR is communicating with your Active Directory instance correctly, then you may find users are unable to login.
Base Group Domain Name
The value here can be left blank, in which case the root of the Active Directory tree will be used as the root of searching for users. However to be more specific you can specify the Organizational Units (OU) and Domain Components (DC) to search within. It is likely you will need to specify the Domain Components. Please note that the order of the components is very important here.
When specifying OUs they are typically listed in reverse order, with the lowest-level OU specified first which aligns with the hierarchical nature of how these units are defined within AD. The DC elements are listed in a more natural left-to-right order.
By way of example, if you wished to search in the Domain Component "bisorg.external" and under that domain, there was the hierarchy of the Organizational Unit "fusion" with the Organizational Unit "Registry" within that, then the following string, with its elements in the following order, would be used:
OU=Registry,OU=fusion,DC=bisorg,DC=external
User Search Filter
This field determines how the FMR will locate users within the AD tree. The syntax of valid values can be located on the Microsoft support site. FMR will not validate the contents of this field for syntactical correctness and will simply use what is entered.
If this field is left blank, the following value will be used:
(&(objectClass=user)(userPrincipalName={0}))
This states that the search filter is looking for objects in Active Directory of class "user" and where the User Principal Name of those objects is the value as specified by {0}. {0} is a placeholder for the value the user types in to FMR in order to become authenticated, however there are some subtleties. In the User Search field there are two placeholder values:
- {0} - is the "bind principal". This is the username that the user types into the login dialog (when attempting to login). However if this value does NOT contain an "@", then the domain name is appended to it. For example, if the user attempts to log in as "Alice", on the domain "bisorg.external", then the value that replaces {0} will be Alice@bisorg.external
- {1} - is the "username" only. This corresponds exactly to the username. If the user attempts to log in as "Alice", then the value that replaces {1} will be simply "Alice".
By way of example, the following specifies a search for objects of class "user" where the User Principal Name in AD will be the "bind principal". If this is not resolved, then the sAMAccountName is checked against the username:
(&(objectClass=user)(|(userPrincipalName={0})(sAMAccountName={1})))
Testing the Active Directory Settings
Since it can be difficult to set the Active Directory settings correctly, since version 11.17.0 of FMR, there is also the ability from this page for an Admin user of FMR to test how Active Directory would respond with an attempted log-on for a particular user. This feature allows for quicker investigation and resolution of the Active Directory settings that you will require for your environment.
Clicking the "Test Settings" control displays a section of the page allowing the systems admin to enter a userid and password. Note that the other AD settings can be modified during this time allowing for experimentation.
When the blue "Test User" button is clicked , the system attempts to authenticate the user specified in the lower section. Here are some sample responses:
Examples of unable to communicate with the AD system:
Example of incorrect password for the user:
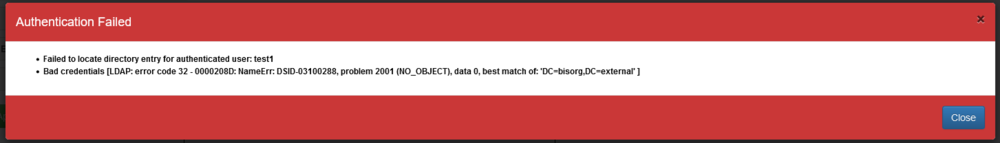
Example of incorrect AD - the user couldn't be located since the Base Group DN was incorrect:
Example of too many users being found. There must be a unique user for the specified userid

Example of correct credentials:
Other Active Directory Tools
If you are still having issues determining what your settings should be for Active Directory, then the Windows Powershell commands "Get-ADUser" and "dsquery" may be useful to you.
dsquery is a command-line tool in Windows operating systems used to query the Active Directory directory service. Active Directory is a service developed by Microsoft that provides centralized authentication, authorization, and directory services for Windows-based networks. The dsquery command allows administrators to search and retrieve information from Active Directory. It can be used to find various objects such as users, groups, computers, and organizational units (OU).
If you wish to find a particular user, you can use the command:
dsquery user -samid <username>
It can also allow you to test your search filter, such as in the following manner, which obtains the Base Group DN for the user 'test1'
dsquery * domainroot -filter "(&(objectClass=user)(userPrincipalName=test1*))"
"CN=test1,OU=users,OU=Registry,OU=fusion,DC=bisorg,DC=external"
The Windows PowerShell command Get-ADUser allows the retrieval of a user's information. So to see what the sAMAccountName is for a particular user, you can use:
Get-ADUser -Identity "username" | Select-Object SamAccountName
Next Steps
It is likely that you will wish to create Role Mappings for your users. Please refer to the Role Mappings page for further information.