Difference between revisions of "Configure X509 Certificate Authentication"
(→Authentication via Certificates) |
(→Authentication via Certificates) |
||
| Line 1: | Line 1: | ||
[[Category:FMR_Configuration_Reference]] | [[Category:FMR_Configuration_Reference]] | ||
[[Category:How_To]] | [[Category:How_To]] | ||
| − | + | =Authentication via Certificates= | |
Fusion Meta Data Registry (FMR)supports authentication via the use of an X509 certificate (in the PKCS12 format).<br> | Fusion Meta Data Registry (FMR)supports authentication via the use of an X509 certificate (in the PKCS12 format).<br> | ||
| Line 14: | Line 14: | ||
New Certificates are added by clicking on the cogs icon and selecting Create New Certificate Definition. | New Certificates are added by clicking on the cogs icon and selecting Create New Certificate Definition. | ||
| − | [[File:Certificate Manager Page.PNG|Authentication | + | [[File:Certificate Manager Page.PNG|1000px]] |
| + | |||
| + | =Certificate Authentication Setup Procedure= | ||
| + | ==Generating Self-Signed Certificates== | ||
| + | ===Overview=== | ||
| + | The following gives an example of how to create self-signed certificates these certificates will be used for applications to authenticate with the tomcat server. | ||
| + | |||
| + | Whilst trusted authorities such as Verisign are typically used to generate Certificates for website to run under https, a self-signed Certificate can be generated locally using applications such as Java Keytool, which is freely available as part of the Java JDK distribution (under Java/bin). | ||
| + | |||
| + | Self-signed certificates will not be trusted by web browsers, as they have not been created by a trusted authority, however for internal use, to distribute to users of an application, they are perfectly adequate (if you trust yourself). | ||
| + | |||
| + | ===Generate a certificate for the client of Fusion Registry=== | ||
| + | |||
| + | This process creates a self-signed certificate to be given to the user of the Fusion Registry. This certificate contains the user’s username in the Certificates Common Name (CN). This process consists of two steps as follows: | ||
| + | |||
| + | Generate a p12 file which contains the private key and certificate. This generation step prompts a number of questions on the command line. The first question is ‘what is your first name’ this value here should be the username of the user that the certificate will be issued to. | ||
| + | |||
| + | keytool -genkeypair -alias regClient -keyalg RSA -validity 365 -keystore regClient.p12 -storetype PKCS12 | ||
| + | |||
| + | [[File:Example p12.PNG}800px]] | ||
| + | |||
| + | Export the certificate from the p12 file to a .cer file | ||
| + | |||
| + | keytool -exportcert -alias regClient –keystore regClient.p12 –storetype PKCS12 –file regClient.cer | ||
| + | |||
| + | |||
| + | |||
| + | |||
| + | |||
| + | |||
| + | |||
| + | |||
| + | |||
| + | The certificates created in this example are not the same certificates that are used to enable Tomcat to run under https. | ||
| + | |||
| + | It is assumed that the Certificate to enable https will be generated by a trusted authority, and that Tomcat has already been configured to run under https. | ||
| + | |||
| + | This process makes use of '''Java Keytool''' this is a command line application for certificate creation and management. | ||
Revision as of 03:29, 21 July 2022
Contents
Authentication via Certificates
Fusion Meta Data Registry (FMR)supports authentication via the use of an X509 certificate (in the PKCS12 format).
The Web Application Container WAC (e.g. Tomcat) must be configured to trust the certificate as the WAC is responsible for authenticating the Certificate.
Certificate Authentication will only work if HTTPS is enabled (is this correct - if so where do you do that?
When the request is passed onto the FMR, it will attempt to map the Certificate to a FMR user.
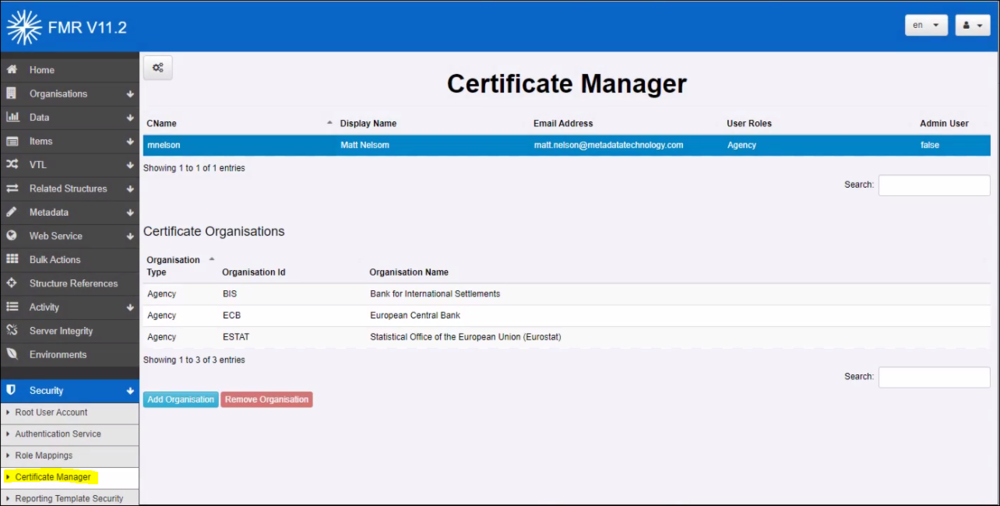
To support a new Certificate, log into the FMR as an Admin user, and navigate to Security -> Certificate Manager.
New Certificates are added by clicking on the cogs icon and selecting Create New Certificate Definition.
Certificate Authentication Setup Procedure
Generating Self-Signed Certificates
Overview
The following gives an example of how to create self-signed certificates these certificates will be used for applications to authenticate with the tomcat server.
Whilst trusted authorities such as Verisign are typically used to generate Certificates for website to run under https, a self-signed Certificate can be generated locally using applications such as Java Keytool, which is freely available as part of the Java JDK distribution (under Java/bin).
Self-signed certificates will not be trusted by web browsers, as they have not been created by a trusted authority, however for internal use, to distribute to users of an application, they are perfectly adequate (if you trust yourself).
Generate a certificate for the client of Fusion Registry
This process creates a self-signed certificate to be given to the user of the Fusion Registry. This certificate contains the user’s username in the Certificates Common Name (CN). This process consists of two steps as follows:
Generate a p12 file which contains the private key and certificate. This generation step prompts a number of questions on the command line. The first question is ‘what is your first name’ this value here should be the username of the user that the certificate will be issued to.
keytool -genkeypair -alias regClient -keyalg RSA -validity 365 -keystore regClient.p12 -storetype PKCS12
[[File:Example p12.PNG}800px]]
Export the certificate from the p12 file to a .cer file
keytool -exportcert -alias regClient –keystore regClient.p12 –storetype PKCS12 –file regClient.cer
The certificates created in this example are not the same certificates that are used to enable Tomcat to run under https.
It is assumed that the Certificate to enable https will be generated by a trusted authority, and that Tomcat has already been configured to run under https.
This process makes use of Java Keytool this is a command line application for certificate creation and management.